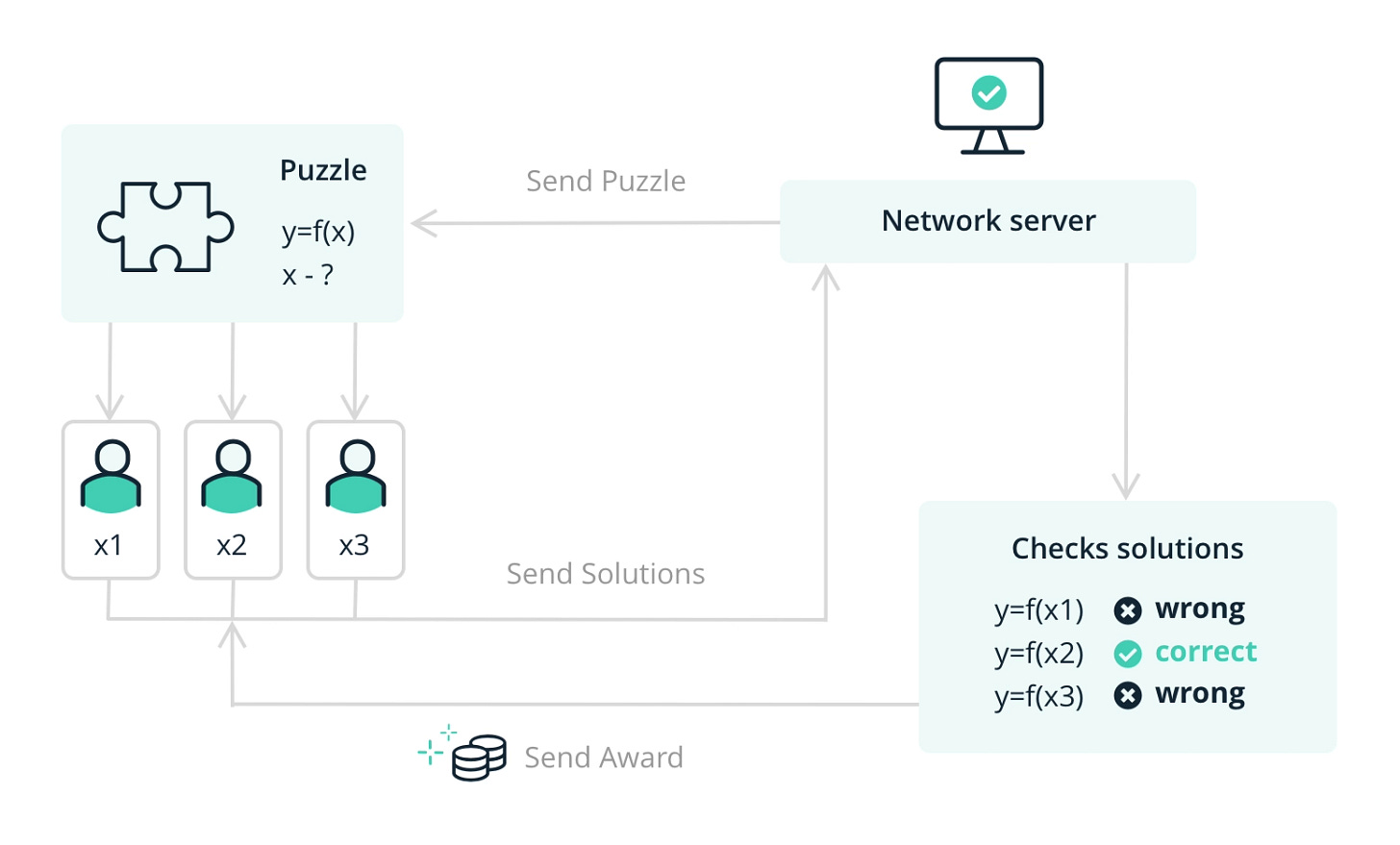
Proof-of-Work (POW) Algorithm - Introduction
Blockchain can be divided into the public chain and license chain, which is determined by the node premissions. Public blockchains are permissionless and allows anyone to join, thus making them decentralized. This allows all nodes of the blockchain to have equal rights to access the blockchain and participate in activities (i.e. creating new blocks of data, validating those blocks, etc). The main use case for public blockchains has to do with exchanging and mining.
Private blockchains, also referred to as managed blockchains, are blockchains with special access restrictions usually controlled by an organization. Such that, the central authority will determine who can be a node.
There are also consortium and hybrid blockchains, which we will save for another post.
Proof-of-Work (POW)
The probability of obtaining rights by consuming computing power
The greater the computing power, the higher the probability
Advantages: Strong randomness and fairness
Disadvantages: Energy consumption and low consensus efficiency
This algorithm was developed from the idea of Hashcash. It is primarily used to create stamps to attach to mail and add a micro-cost to sending mail to deter spamming. Proof-of-Work (POW) can be broken down into two sides (1) certifier and (2) verifier, which work in conjunction to complete verifiable computing tasks. Now the certifier provides material to the verifier to prove that (x) number of calculations were completed in (y) amount of time.
Application of POW in Bitcoin (from Nakamoto)
New transactions are broadcast to all nodes
Each node collects new transactions into a block
Each block works on finding a difficult proof-of-work for its block
When a node finds a proof-of-work, it broadcasts the block to all nodes
Nodes accept the block only if all transactions in it are valid and not already spent
Nodes express their acceptance of the block by working on creating the next block in the chain, using the hash of the accepted block as the previous hash
In the bitcoin network, given a value D, there is a block that contains all transaction data.
SHA-256: Is a hash function that takes an input of a random size and produces an output of a fixed size. It can be used in two different ways: (1) mining or (2) creation of bitcoin addresses
The SHA-256 algorithm is also used to produce the merkle root, which is then later inserted into the block header. After the construction of the block is successful, the miner will begin the process (also brings up another use case of this algorithm).
The Nonce:
One parameter of the block header
A variable that is changed repeatedly
If the hash is below the target, the miner is successful (SHA-256 helps with hashing the block header)
We will continue this topic tomorrow. I like keeping my posts short and simple for others.